Trust Problems - E03 - Security is a process not a state
This third edition of my series explores trust issues that arise when security is viewed as an ongoing process rather than a state. On the Example of PQC
Whilst reading this great blog post [1] regarding the current State of Post Quantum Cryptography (PQC) I got the idea to write this blogpost.
What is PQC anyway? #
Generally speaking PQC refers to the class of cryptographic algorithms, that are designed to be secure against attacks
from quantum computers.
These are necessary because quantum computers have the potential to solve certain mathematical problems much more
efficiently than our current computers.
These problems include integer factorisation and discrete logarithms.
This fact poses a problem particularly because our currently used cryptographic systems, such as RSA and ECC, are based
precisely on these mathematical approaches.
It should be noted at this point that both RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) are
asymmetric cryptography systems.
This means that the asymmetric cryptography systems we currently use are so easy to break by quantum computers that they
can no longer be considered secure.
Accordingly, as soon as quantum computers are powerful enough (currently assumed to be 5-10 years), asymmetric
encryption (based on current crypto systems) will be regarded as compromised.
At the same time, as things stand, symmetric algorithms such as AES (Advanced Encryption Standard) are not threatened by
quantum computers.
Why is there already a risk? #
Ok, as things stand, quantum computers are not able to break these asymmetric crypto systems. So why should I worry now?
Harvest Now, Decrypt Later
The particular interesting part is that we can not only intercept communication right now, but rather that we are able
to easily capture current encrypted communication.
Since currently there is no way to break asymmetric encrypted messages, these algorithms are considered secure and
therefore widely used.
But as the ability to decrypt these messages has arrived at the horizon, some actors have started collecting encrypted
traffic/messages.
And as always this is not about your friends decrypting your mothers warning to pack a warm jacket for your trip to
Scotland...
Rather this can be applied to the field of industrial spionage or nation state actors - or in short any point where
either big sums of money or power are involved.
In the context of state affairs or in industry, there may well be information that is still highly explosive in over a
decade's time.
But let us be honest this applies to anyone exposed in the public from politicians to scientists.
What does that have to do with security as a state? #
I would like to use this fundamental dilemma as a hook to point out that security is not a state but an ongoing process. This requires regular checks and adjustments, similar to a control loop such as the PDCA-cycle.
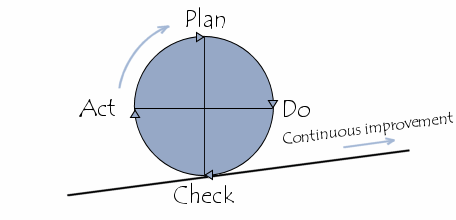
The fact that our algorithms, which were previously classified as secure, will no longer be secure in the future, with the usability of quantum computers, is therefore already a problem today.
What can we do about that? Takeaway #
Cryptographers are already aware of this dilemma.
For this reason, algorithms are being developed that cannot be broken by quantum computers, as they are based on other
classes of mathematical problems.
These include hash-based, lattice-based, code-based, and multivariate polynomial-based methods (I will not present these
further in this article; they may be the subject of a follow-up article).
Another approach is to use previously developed PQC algorithms in a hybrid model today.
Here, the key exchange takes place as part of the communication setup with the help of a PQC algorithm.
The subsequent communication takes place using a symmetric algorithm via the previously exchanged key.
This avoids the future uncertainty of current asymmetric algorithms.
[1] - Post Quantum Cryptography,
Netmeister
[2] - Deming Cycle
Explained [with an example], Abhinav Kaiser